Threat detection systems encompass a range of technologies and techniques employed to identify and respond to potential security threats. These […]
Author: admin
Essential Endpoint Defense and Response Strategies for Enhanced Cybersecurity
Endpoint defense and response encompasses security measures designed to protect endpoints, such as laptops, desktops, and mobile devices, from cyber […]
The Ultimate Guide to Advanced Security Monitoring for Cybersecurity Pros
Advanced security monitoring is the practice of using advanced technologies and techniques to monitor security events and data in an […]
Ultimate Guide to Security Threat Detection: Safeguard Your Cyber Stronghold
Security threat detection is the process of identifying and responding to potential threats to an organization’s security. These threats can […]
The Ultimate Guide to Advanced Threat Detection for Bulletproof Cybersecurity
Advanced threat detection is the process of identifying and responding to sophisticated and targeted cyberattacks. These attacks often use novel […]
Ultimate Guide to Host-Based Security Systems for Enhanced Cybersecurity
A host-based security system is a type of security system that is installed on a computer or other device. It […]
Ultimate Endpoint Protection: Shielding Your Network from Cyber Threats
Endpoint protection is a cybersecurity solution that safeguards individual devices such as laptops, desktops, and mobile phones from malware, viruses, […]
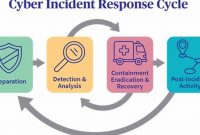
Ultimate Guide to Cyber Incident Response for Enhanced Cyber Security
Cyber incident response is the process of responding to and recovering from a cyber incident. It involves identifying the incident, […]
Revolutionize Cybersecurity with Automated Threat Detection
Automated threat detection is the process of using software tools to identify and respond to potential threats in a timely […]
Effective Incident Management: Strategies for Enhancing Security and Mitigating Risks
Incident management is a systematic approach to managing unplanned interruptions to an organization’s services or operations. An incident can be […]