Security intelligence refers to the process of gathering and analyzing data to identify, prevent, and respond to security threats. It […]
Author: admin
Comprehensive Endpoint Threat Intelligence: Protect Your Devices
Endpoint threat intelligence gathers and analyzes data to provide comprehensive insights into potential threats and vulnerabilities at endpoints, which are […]
Master Security Information Management for Unstoppable Cyber Defense
Security information management (SIM) is the process of collecting, analyzing, and reporting on security-related information from multiple sources within an […]
Essential Malware Prevention: Safeguard Your Systems from Cyber Threats
Malware prevention refers to the proactive measures taken to protect computer systems, networks, and devices from malicious software, known as […]
The Ultimate Guide to Security Orchestration for Enhanced Cybersecurity
Security orchestration, a vital aspect of modern cybersecurity, enables organizations to automate and coordinate their security tools and processes, enhancing […]
The Definitive Guide to Incident Detection and Response in Modern Cybersecurity
Incident detection and response is the process of identifying and responding to security incidents. It involves detecting suspicious activity, investigating […]
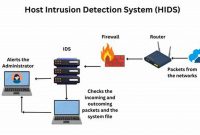
Comprehensive Guide to Host Intrusion Detection: Shield Your Networks from Cyber Threats
Host intrusion detection systems (HIDSs) monitor a host computer or network for suspicious activity. They can detect a variety of […]
The Ultimate Guide to Threat Mitigation: Protecting Your Digital Assets from Cyber Attacks
Threat mitigation is the process of identifying, analyzing, and mitigating threats to an organization’s assets. It is a critical part […]
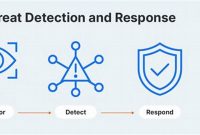
Comprehensive Guide to Threat Detection and Response: Protecting Your Digital Assets
Threat detection and response is the process of identifying and mitigating cybersecurity threats. It involves monitoring and analyzing network traffic, […]
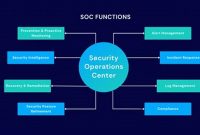
Security Operations: The Essential Guide to Securing Your Organization
Security operations encompass the practices and processes employed to protect an organization’s assets from security breaches and cyberattacks. It involves […]